Secure document management in large organizations: Building Data Trust

In this blog, we explore how large organizations can securely manage and govern their documents. At Epical, we see this as a vital component of what we call Data Trust. For us, Data Trust is about more than just secure handling—it's about ensuring that data is managed responsibly and transparently.
We define Data Trust as:
"Handling data in a trustworthy and responsible manner to safeguard the privacy, security, and ethical use of data collected from individuals or other entities."
The purpose of establishing Data Trust is to build confidence among all stakeholders—customers, partners, and the public—by demonstrating transparency and accountability in data security and management.
Why focus on document management?
In many organizations, documents are poorly managed, even though they contain sensitive business information, internal data, or even information governed by laws such as the Data Act, GDPR, or the AI Act. This makes secure document management crucial, as documents carry significant value and risk.
While there are many technical solutions available, we believe technology isn't the best starting point. Instead, organizations should begin by defining what they want to achieve and establishing clear priorities.
The home/fortress vs. Out-of-home metaphor
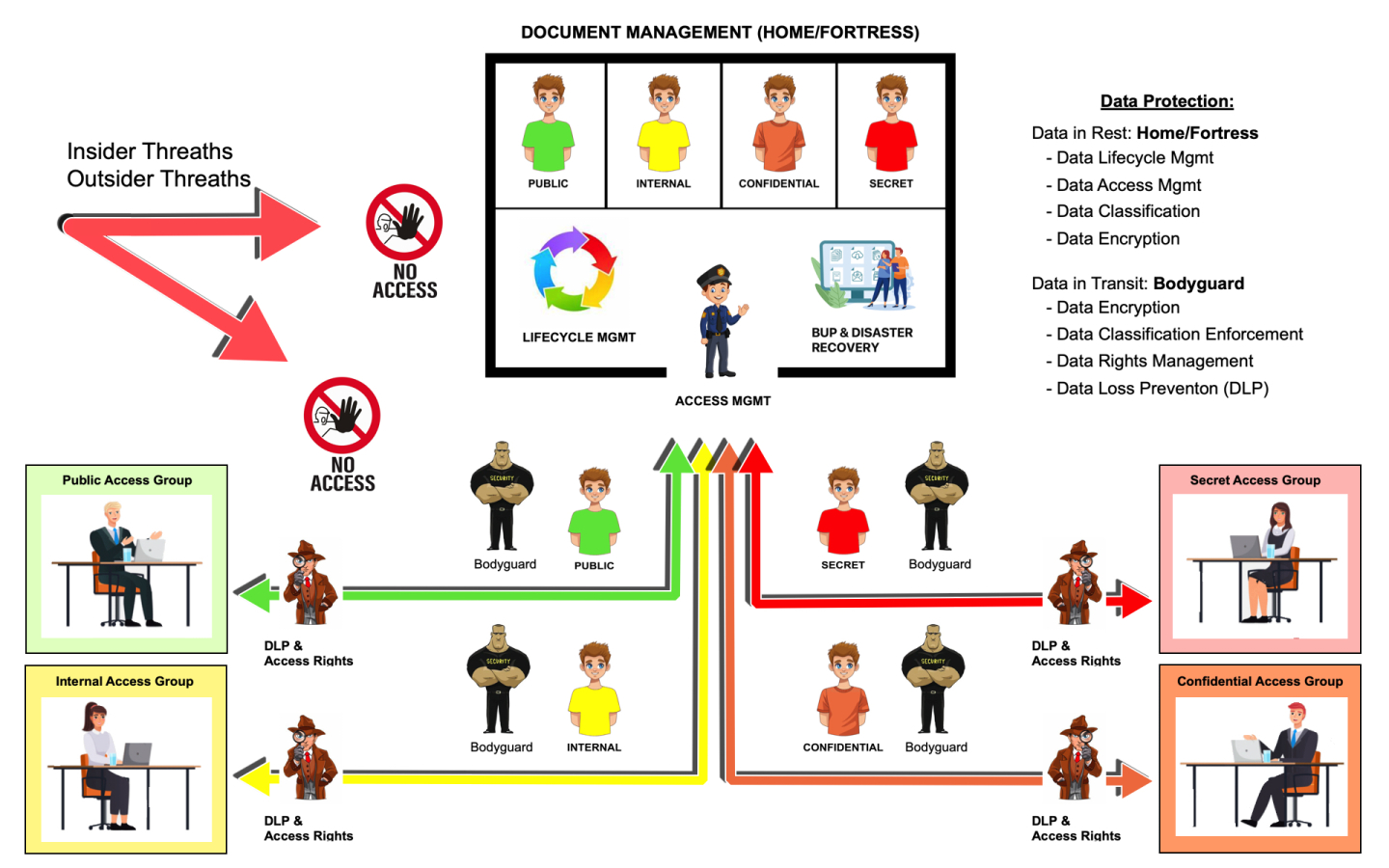
Just as your home protects your family from external threats, your document management system (DMS) must protect your organization’s sensitive documents from both internal and external risks. These threats could include unauthorized access to confidential information or a ransomware attack that locks down critical files.
A well-implemented document management system supports the life cycle of documents while also enforces robust security controls. Document management is not a black-and-white process. Some functions, such as retention management, automatically delete sensitive documents after a certain period, reducing the number of sensitive documents at risk of being disclosed. Fewer documents mean fewer security risks and make it easier for users to find the documents they need.
To build an effective document management system, organizations need to support the entire document life cycle—from creating the right templates to storing documents in the correct location, with proper tagging or markup. This ensures that everyone who needs to access the document can find it easily, with the added benefit of fewer documents to sort through. Although there’s a lot more to the document life cycle, the focus in this article is on security.
Key security features of a document management system
A robust document management system (DMS) offers multiple layers of security to protect sensitive information at every stage of its lifecycle. Below are the key features that ensure documents are securely managed.
-
Access rights: The first layer of protection controls who can interact with documents. These rights are often set at the container level, applying to all documents within that container.
-
Document classification: Documents should be classified based on their sensitivity and associated risk. Classification often dictates the security controls applied, including encryption, which restricts access to authorized users only.
-
Additional security controls: These can limit actions such as editing, renaming, printing, and copying text or data.
-
Data-in-transit protections: When documents leave the DMS, they are at greater risk. Here, it's critical to apply controls that ensure the document remains secure, even outside the system. External users, for instance, may have limited access, with restrictions on downloading, printing, or sharing files.
-
Data loss prevention (DLP): To prevent unauthorized sharing or leakage of sensitive information, Data Loss Prevention (DLP) mechanisms can be applied. DLP tools monitor the movement of sensitive documents, ensuring that they cannot be shared externally or moved to untrusted locations without proper authorization.
By ensuring documents are secured both in-residence (Data-in-Rest) and while being accessed or shared externally (Data-in-Transit), organizations can maintain high levels of protection. Remember, the weakest link will always define the strength of your security.
In addition, during any disruption or disaster, it’s essential to have recovery plans and processes in place. These should be well-protected and readily accessible to ensure a quick return to business continuity.
What does a technical solution look like?
When considering technical solutions, it's important to remember that the tools vary depending on your needs.
Create the data security roadmap
When thinking about your documents from a security perspective, it’s important to consider two things:
-
Compliance with internal and external regulations.
-
Resilience against cyberattacks and internal threats.
While this may sound simple on the surface, at a granular level, it’s complex. The key is to prioritize where to start and what to do next. That’s why we recommend using a goal model to break down tasks and prioritize actions.
The goal model: Doing the right things in the right order
A goal model helps define what needs to be achieved and why. It provides a structured approach that aligns with your business goals. At the top of the model sits the overarching vision, followed by impact goals, project goals, product goals, and resource goals.
For each goal, look upward to understand why it exists. If no matching overarching goal exists, either remove it or add a relevant one. Then, look downward to ensure all necessary steps to fulfill the goal are in place. This process helps you prioritize, eliminate redundant efforts, and set a time frame for achieving specific objectives.
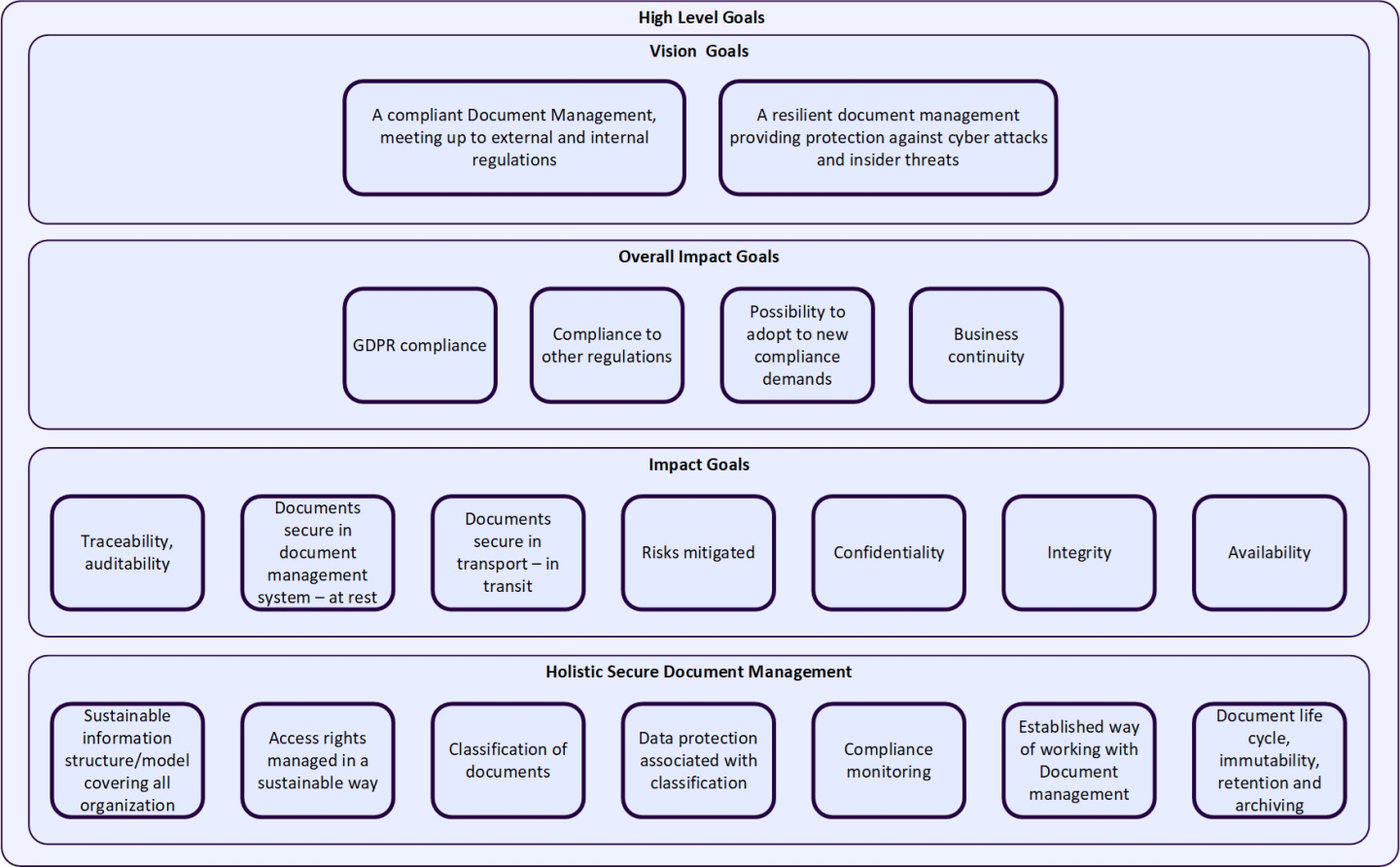
The goal model works by organizing your objectives into a clear hierarchy. Start with the visionary goals—the “why” behind your efforts. From there, look downward to understand how these goals can be achieved by setting overall impact goals. Prioritize the most important ones. All of these goals can then be broken down into sub sections with what is needed to be done to reach each goal. By doing this, you ultimately develop a roadmap that will take your organization to a better level of data security in document management.
Ready to build your roadmap to secure document management?
Reach out to us at Epical.
Authors:
Tomas Wulfing, Business Architect, Epical
Mika Käck, Principal Consultant, Epical
Kim Söderström, Security Architect, Epical


